Many instances of cyberattacks have demonstrated that smart contracts, like blockchain technology, are vulnerable to hacks and exploitation. The total amount of money stolen or lost as a result of smart contract errors is in billions of dollars. The following are some of the most significant instances of smart contract code errors:
Smart contracts are self-executing contracts, in which the provisions are stipulated in the code.
For example, an Ethereum smart contract is deployed as one or many transactions on the Ethereum blockchain which then runs on the Ethereum virtual machine, a blockchain-based platform. The smart contract can be called by a user, by using a blockchain transaction. This transaction calls for a pre-defined procedure on the smart contract, granting the user access to the information contained within it.
For example, a vending machine operates on “contract” logic. The operation of dispensing a product is only fulfilled when a user puts money in the machine and chooses the product. Smart contracts are, of course, employed in a more complex manner when conducting cryptocurrency transactions.
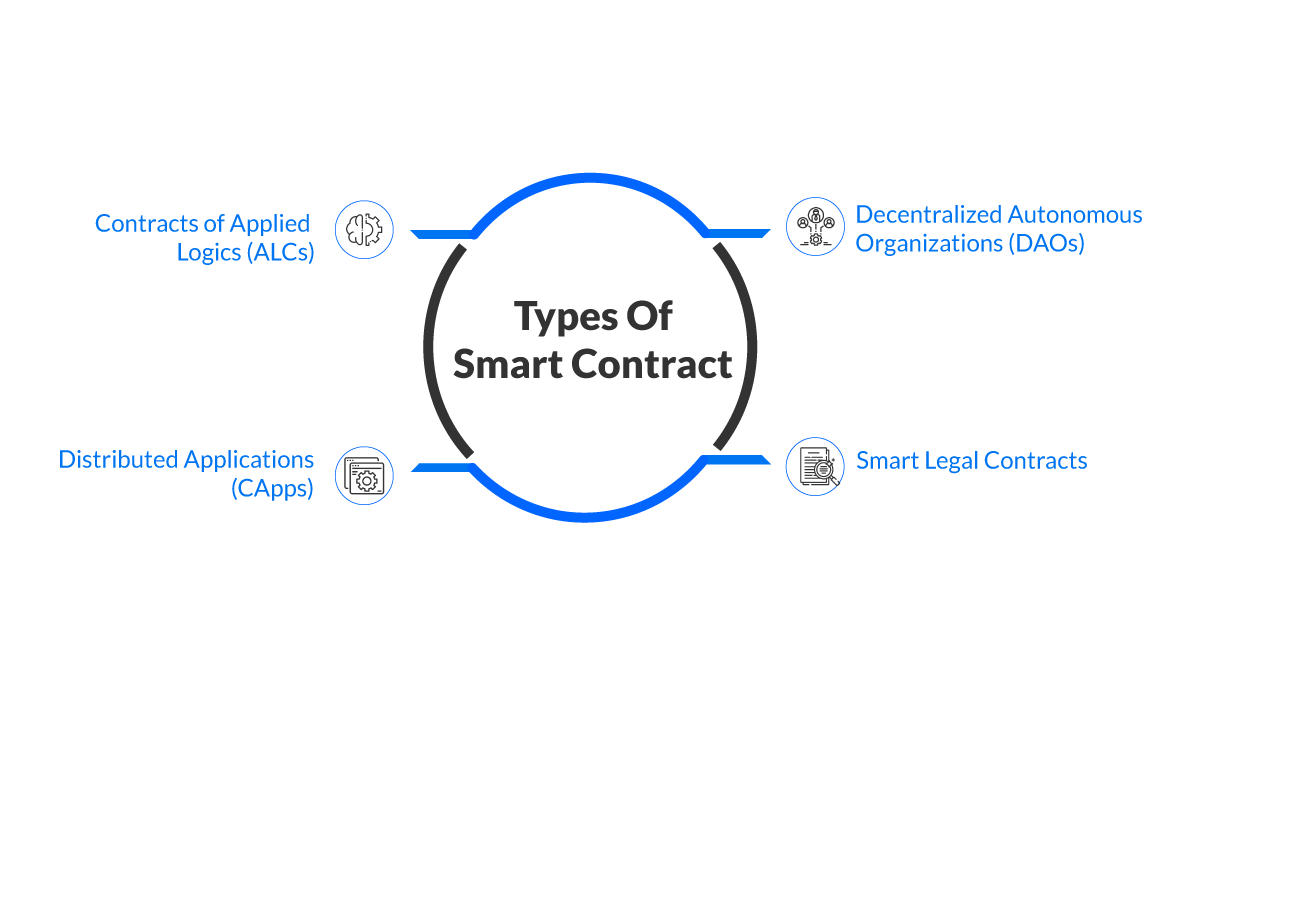
Smart contracts are designed, constructed, and deployed over a network using programming languages like Solidity and Vyper. Smart contacts come in varied flavors, some of the most used types are –

Solidity contracts tend to transfer significant amounts of value as one of their core functions, in contrast to many conventional programming languages. As a result, they are vulnerable to several high-risk attacks from attackers looking to siphon money from these immutable actors.
Let us quickly review the main vulnerabilities:
As a result, if a vulnerable contract X makes an external call to an untrusted contract Y, the latter may be maliciously modified to make a recursive call back to the weak contract X. Contract X might essentially run out of resources before the function is finished if the call from contract X to contract Y includes transmitting any amount of ether.
One unintended consequence of this design is that a smart contract’s intended conclusion is publicly visible before it is validated onto the blockchain. This transaction might be seen by malicious actors scanning the mempool, who might then take advantage of the situation by copying your smart contract and submitting it at a higher value. Then, by submitting their transaction first, they have successfully “front-run” your contract, taking advantage of your arbitrage opportunity.
There are other security obstacles that smart contracts must face in addition to those mentioned above. Smart contracts are frequently vulnerable because not all developers are versed with the semantics of programmable blockchain systems.
In the upcoming blog, we will also be covering key processes involved in securing smart contracts and recommendations at different levels while developing a smart contract.
Business process automation has become an essential part of digital transformation initiatives for enterprises. Almost all enterprise IT decision-makers cite process automation as a critical driver of innovation and necessary in achieving business outcomes. While automating business processes is gaining significant attention, are IT professionals investing enough in automating engineering functions related to Security and DevSecOps? Are they methodically addressing security automation to derive maximum benefits from it?
Commonly, organizations receive thousands or even millions of alerts each month that the security staff must monitor. They must guard a much larger attack surface now with the prevalence of several types of devices, apps, and cloud systems. Manually addressing these threats is almost impossible. Automation becomes increasingly necessary to defend the applications and infrastructure against threats that might slip through the cracks due to human error. In fact, according to a global security automation survey, 80% of surveyed organizations reported high or medium levels of automation in 2021.
This article guides security professionals through various potential areas of security automation and the critical role of DevSecOps in CI/CD pipelines.
Opportunities to automate security functions are limitless, like any other business area. However, a methodical approach to identifying automation areas, besides prioritizing the same based on the frequency of activities, is critical to the success of automation initiatives. The following classification can act as a broad guideline for security automation:
Identifying evasive attacks across security layers by consolidating data from the security environments is the goal of extended detection and response solutions (XDR), a critical method of security operations automation. XDR enables security analysts with data that helps them investigate and respond to various incidents, often directly integrated with standard security tools. Essential automation functions to ensure security across endpoints, networks, and cloud systems include:
A range of vulnerability assessments aims to protect against data breaches and ensure the availability of IT infrastructure. They determine if the system is vulnerable to any known vulnerabilities, give severity ratings to those vulnerabilities, and, if and when necessary, offer remediation or mitigation. The issues of a growing pool of vulnerabilities and limited time available to fix these vulnerabilities are addressed by automating vulnerability scanning. These scanners detect vulnerabilities in a variety of network assets, including servers, databases, applications, regulatory compliance, laptops, firewalls, printers, containers, and so on.
Automated management of responses by orchestrating several operations across security tools is the critical function of Security Orchestration, Automation, and Response (SOAR) methods. SOAR enables security teams to effectively triage alerts, respond quickly to cybersecurity events, and deploy an efficient incident response program. Three key areas of automation include:
As businesses move to public cloud environments that provide on-demand access to computing, networking, storage, databases, and apps, security automation becomes increasingly important. The possible security risks generated by manually setting security groups, networks, user access, firewalls, DNS names, and log shipping, among other things, are eliminated by automating infrastructure buildouts. Further, monitoring security configurations across numerous instances of resources across single, multiple, and hybrid cloud systems is another area where automation is quite helpful in a cloud context.
Providing more ownership to development teams in deploying and monitoring their applications is the goal of DevOps. Automation of provisioning servers and deploying applications is critical for DevOps success. Software applications are complex and can potentially have many security issues ranging from harmful code to misconfigured infrastructure/environments. Integrating security processes and, more importantly, automating them as part of the DevOps workflows is the goal of DevSecOps.
Integration of security automation into the CI/CD pipeline processes without adversely affecting development speed and quality is essential. Automation should enable uninterrupted security compliance checks within the continuous development workflow. Besides, as described in the previous sections, various automation areas apply to the Continuous Operations workflows. Critical automation activities include:
Focus on DevSecOps is increasing as per a survey conducted by GitLabs in 2021. DevOps teams are running more security scans than ever before: over half run SAST scans, 44% run DAST, and around 50% scan containers and dependencies. And 70% of security team members say security has shifted left.
As technology advances, the automation methods applicable for security processes also expand. Teams are leveraging advanced automation techniques on one side while also broadening the scope of automation. Following are the popular techniques followed by enterprises in security automation besides classic opportunistic script-driven automation:
It is worth noting that AI/ML is becoming a reality as the technology matures. It is not a surprise to learn that over 3 out of 4 IT executives in a cybersecurity survey conducted two years ago said that automation and AI maximized the efficiency of their security staff.
Our comprehensive services in Cyber Security and Cloud & DevOps help enterprises significantly enhance their security profile. The following customer success stories demonstrate how we applied advanced techniques for improving security and transforming DevOps:
Digital Transformation of Software Recovery: A self-service and cloud-based PC OS recovery solution.
Our client, a leading PC manufacturer, wanted to address various challenges faced by the consumers when recovering the original PC OS image. Consumers were facing delays in the overall recovery time due to logistics issues or incorrect DVD versions sent at the first instance and the organization was challenged with higher cost of operations and many personnel dedicated to support and manage recovery processes. Chainyard, as an extended team to our client’s team, developed a cloud-based data recovery solution that empowers the end users to independently download device recovery information without the support personnel intervention.
The self-service solution significantly improved customer experience while also reducing the recovery time & costs for the organization.
